The network security that firewalls provide is one of the basic building blocks for a secure cloud infrastructure. We are excited to announce that three new Google Cloud Firewall features are now generally available: Global Network Firewall Policies, Regional Network Firewall Policies, and IAM-governed Tags.
With these enhancements, Cloud Firewall can help you more easily achieve a Zero Trust network posture with a fully distributed, cloud-native stateful inspection firewall service. In the new Global and Regional Network Firewall Policy structures, we expanded the policy structure down to the Virtual Private Cloud (VPC) level, and made it easier and more scalable to deploy and operate. Granular controls enforced at the virtual machine (VM) level using the new Identity and Access Management-governed Tags deliver intra-subnet micro-segmentation with pervasive policy coverage that automatically applies to workloads wherever they are deployed, independently of the network architecture.
The combination of the new policy structures and the IAM-governed Tags delivers a consistent firewall experience across the Google Cloud resource hierarchy, simplifying operations, while also achieving more granular control, enabling a more least-privilege environment, while allowing more self-service for devops for each group or app.
Additionally, we are also introducing some enhancements to our Firewall Insights module within the Network Intelligence Center.
New Network Firewall Policy structures
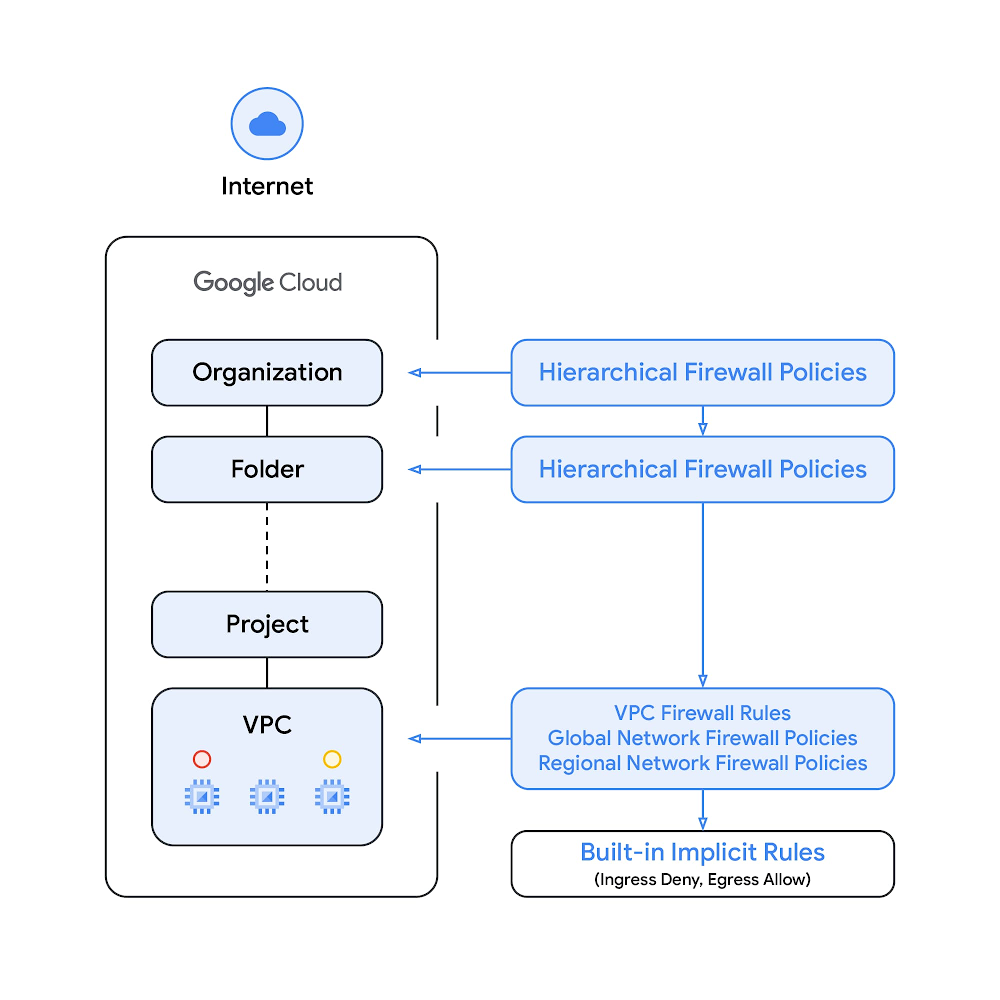
Previously, we introduced Hierarchical Firewall Policies at organization and folder levels. Now we are introducing a new policy structure, Network Firewall Policies, with two types: Global and Regional Network Firewall Policies. This new structure improves upon the previous VPC Firewall Rules structure.
Similar to Hierarchical Firewall Policies, the new Network Firewall Policy structure acts as a container for firewall rules. Rules defined in a Network Firewall Policy are enforced once the policy is associated with a VPC network, enabling simultaneous batch updates to multiple rules in the same policy.
The same Network Firewall Policy can be associated with more than one VPC network, and each VPC network can only have one Global Network Firewall Policy, and one Regional Firewall Policy per region associated with it. Both Global Network Firewall Policies and Regional Network Firewall Policies support IAM-governed Tags, and all Cloud Firewall enhancements moving forward will be delivered on the new Network Firewall Policy constructs.
We will continue to support the previous structure, VPC Firewall Rules, and even support the use of the new Network Firewall Policies and VPC Firewall Rules on a VPC network at the same time. However, we encourage customers to migrate their existing VPC Firewall Rules to Global Network Firewall Policies and Regional Network Firewall Policies.
Check our documentation to read more about Global Network Firewall Policies and Regional Network Firewall Policies.
How are Global Network Firewall Policies and Regional Network Firewall Policies different?
A Global Network Firewall Policy provides a global firewall configuration structure to match the global nature of Google Cloud VPC Networks. It applies to workloads deployed in all Google Cloud regions in the VPC network. A Regional Network Firewall Policy provides a regional firewall configuration structure for Google Cloud Firewalls that can only be used in a single target region. When using Regional Network Firewall Policies, users can designate a target region for a firewall policy. The firewall configuration data will be applied to workloads only in that specific region and will not be propagated to any other Google Cloud regions.
Firewall configuration is considered a critical security configuration for an organization, and Regional Network Firewall Policy can give customers an effective way to define their firewall configuration on a regional basis and can help satisfy data residency compliance requirements, such as those defined in FedRAMP.
Enabling smooth migration from VPC Firewall Rules to Network Firewall Policies
As mentioned above, to enable a smooth process for our customers migrating from existing VPC Firewall Rules to the new Network Firewall Policies, the Cloud Firewall engine supports a hybrid mode allowing both Network Firewall Policies and VPC Firewall Rules to be configured for the same VPC network. In order to avoid disruptions, the rule processing order by default will evaluate the VPC Firewalls Rules before the Network Firewall Policies as illustrated below:
Alternatively, users can swap the evaluation order between VPC Firewall Rules and the new Global Network Firewall Policy, which is our recommended approach once the firewall rule set migration has been completed or for net new customers. Please note that Regional Network Firewall Policies will always be evaluated last, after Global Network Firewall Policies and VPC Firewall Rules.
We developed an automated tool to support migration to Network Firewall Policies. This new migration tool migrates VPC Firewall Rules to Network Firewall Policies in an automated fashion with user input as required. Please reach out to your account team for the latest updates.
IAM-governed Tags integration
Also known as Resource Manager Tags, or just Tags, an IAM-governed Tag is a new type of tag resource with enhanced security properties that can be applied to various Google Cloud resources, including VM instances.
The new Network Firewall Policy structures are built to easily integrate with Tags as a mechanism for enabling micro-segmentation. Unlike Network Tags, Tags are strictly controlled by IAM permissions, allowing enterprises to set up firewall controls without the risk of violation by unauthorized personnel. Using IAM permissions, Tags allow users to define their Network Firewall Policies in terms of logical groupings and delegate the management of those groups within their organization with fine-grained authorization controls.
For example, the assignment of VMs to logical names could be delegated using fine-grained IAM controls to other teams in the organization such as app developers, database administrators, or operations teams. Unlike the Network Tags that are mapped only to the primary IP address of a VM, the new Tags in Network Firewall Policies support both primary and alias IP range mapping. Tags replace Network Tags as the recommended, best-practice tagging mechanism in defining firewall rules for VM instances.
Benefits of IAM-governed Tags
Tags provide the following benefits to our customers:
-
Fine-grained IAM Controls: IAM authorization policies can be used to restrict which users are allowed to modify tags and which users are allowed to bind individual tags.
-
Scalability: Users can create a maximum of 1,000 tag keys in an organization, with a maximum of 1,000 tag values per tag key. Each tag value can be attached to an unlimited number of VM instances.
-
Anti-spoofing protection: When VM instances communicate, tag-based firewall policies are enforced using the identity of the sender, even if the source VM is configured to allow spoofing of the source IP of the traffic it originates.
-
Reference across peer networks: tags associated with workloads in one VPC network can be referenced in Firewall Rules for its peer VPC network to provide name-based rule control for inter-VPC network traffic.
-
More control over tagging: Users can attach up to 10 tags per VM per VPC.
Benefits of leveraging Network Firewall Policy with IAM-governed Tags instead of Network Tags and Service Accounts
Our previous recommendation for network security and micro-segmentation used VPC Firewall Rules, Network Tags, and Service Accounts to protect workloads. Network Tags do not include built-in IAM governance, so these tags can be added to any VM instance, which leaves the possibility of tag misuse from insider threat actors.
While Service Accounts come with better IAM control, only a single service account can be associated with each VM, limiting the flexibility of categorizing the workload in multiple dimensions for more flexible access controls to be applied. If changes to the Service Account are required, the VM would have to be shut down and recreated, which is not ideal for production workloads.
The Service Accounts and Network Tags could not be referenced from a different VPC, so the only method of inter-VPC network traffic control with the prior implementation was using IP addresses. In addition, the VPC firewall rules need to be updated individually at each rule level, and no batch update is supported, leading to race conditions and operational challenges.
With the introduction of Network Firewall Policies, users can enjoy the following benefits:
-
Batch editing of multiple rules within a single policy, which saves time, simplifies rule management, and eliminates race conditions created by single rule update patterns.
-
A single resource to contain all the firewall rule sets applied to a VPC network, making it possible to manipulate the firewall configurations with unified APIs on the single resource.
-
Support for separate IAM permissions governing policy creation, update and association to allow enterprises to implement more granular IAM controls based on their needs and requirements.
-
Sharing and attaching of firewall configurations across VPC networks in the same project, which significantly simplifies the configuration and management.
-
Support for IAM-governed Tags
Moving forward, we would recommend using the Network Firewall Policies combined with tags to enable micro-segmentation.
Firewall Insights: Custom Refresh Cycle and IPv6 Support
Firewall Insights in Network Intelligence Center offers automated analysis to identify firewall rule configuration issues. We are very excited to announce the general availability of two enhancements – Custom Refresh Cycle for Shadowed Rule Insight generation, and IPv6 Support.
Previously, the Firewall Insights service was designed to run at a fixed schedule (every 24 hours) to detect customers’ firewall rule changes and update insights when there was a change detected. With Custom Refresh Cycle support, customers are now allowed to define their own insights refresh frequency based on their operational cycle and capacity in order to help optimize the return on investment.
Additionally, the expansion of IPv6 rule support allows users to analyze IPv6 rules in the same way as IPv4 rules during their IPv6 adoption process.
Conclusion
The new policy constructs, Global and Regional Network Firewall Policies and IAM-governed Tags provide a new, foundational set of capabilities for our fully distributed, cloud-native firewall service. They allow simplified, more granular control of firewall policies with better scale. When combined with Hierarchical Firewall Policies, they can help create an environment that can be least-privileged in security posture, while also being self-service for teams throughout the organization. You can learn more about all these new capabilities in our product documentation.