Trusted Internet Connections (TIC) is a federal cybersecurity initiative established in 2007 to enhance network and boundary security across the federal government. The initial versions of the TIC initiative established a network security baseline by requiring agencies to consolidate and monitor their external network connections. The TIC 2.0 initiative focused on securing traffic at the physical agency network perimeter through traditional TIC access points that operate EINSTEIN3 sensors provided by TIC Access Providers (TICAP).
This model created challenges for federal cloud deployments due to the requirements to route all external traffic through approved TIC access points that reside outside of the cloud. With the increased demands on bandwidth, transport encryption, and scalable connections, the TIC initiative caused cloud services to increase in cost and degrade in performance. In 2017, the report to the President on Federal Information Technology Modernization identified the TIC initiative as a barrier to cloud adoption.
In 2019, The Office of Management and Budget (OMB) released the M-19-26 memo to provide enhancements on the TIC initiative. The new TIC version 3.0 broadens the concepts of the program to accommodate cloud and mobile applications, services, and environments. The TIC 3.0 program now envisions a flexible perimeter or multi-boundary versus the hard perimeter previously conceptualized.
One of the primary goals of the TIC modernization effort is to move from a consolidated model toward distributed architectures to promote cloud adoption. The new model can provide agencies with the flexibility to implement security capabilities consistent with their mission and risk tolerance and enforce them in policy enforcement points (PEP) in the cloud.
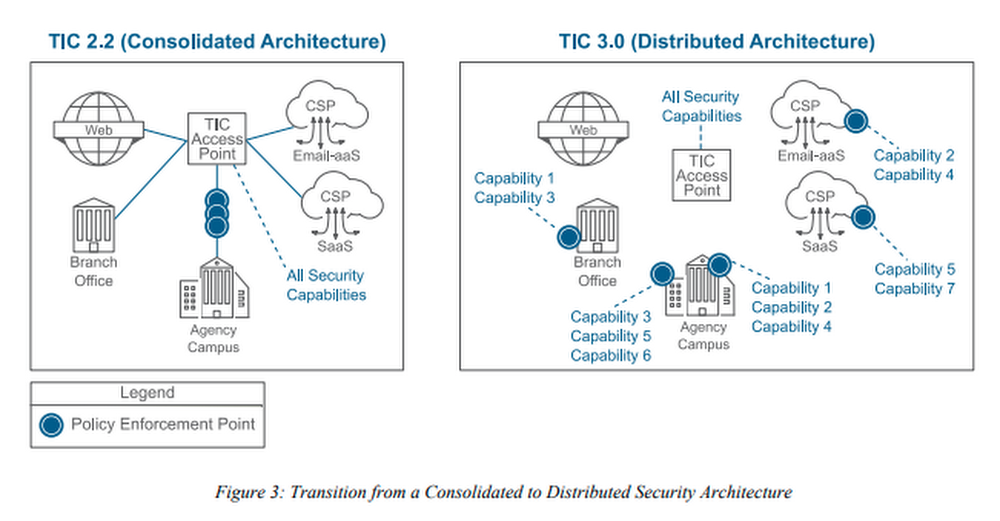
*Transition from a Consolidated to Distributed Security Architecture as outlined in CISA’s TIC 3.0 Program Guidebook.
As part of our commitment to supporting Federal Agencies, we are excited to share several resources to help agencies design and deploy TIC 3.0 compliant solutions on Google Cloud. We prepared these artifacts to align with the controls, use cases, and assumptions provided in the Cybersecurity & Infrastructure Security Agency (CISA) TIC 3.0 core guidance documents.
Check out the TIC 3.0 resources below:
TIC Overlay Handbook
The TIC 3.0 Overlay Handbook – Google Cloud Service Mapping is intended to align the TIC security capabilities, described in the TIC 3.0 Security Capabilities Catalog with available Google Cloud services and partner products. The overlay consists of a series of tabs that map TIC universal security capabilities or Policy Enforcement Point (PEP) security capabilities to available Google Cloud products and services. The Overlay Handbook is intended to provide a high level mapping and can be used by agencies to assess the capabilities of Google Cloud to meet their applicable TIC 3.0 security objectives and mission needs.
Note:The TIC 3.0 Overlay Handbook – Google Cloud Service Mapping maintains version consistency with Ver 2.0 of the Security Capabilities Catalog published by CISA. When CISA updates the Security Capabilities Catalog version, Google Cloud will update the TIC 3.0 Overlay Handbook – Service Mapping accordingly.
TIC Capability to Google Cloud Services – Control-Level Mapping
For those interested in a more granular, control-level mapping, the TIC Capability Mapping (CSF to GCP Services by FedRAMP controls) document maps each TIC capability to the relevant NIST 800-53 rev 4 controls and includes a description of Google Cloud services that can be used to address the TIC capabilities. This was created by first mapping TIC capabilities to NIST Cybersecurity Framework (CSF) controls, then by mapping the NIST CSF controls to NIST 800-53 rev 4 and finally mapping NIST 800-53 rev 4 to Google Cloud services. This document can help agencies assess how Google Cloud native capabilities address their requirements and where 3rd party products may complement native services.
TIC Reference Architectures and Use Cases
The detailed reference architecture use cases below show applicable cloud security patterns, high level design, and detailed network diagrams. The purpose of these documents is to provide guidance to design and support implementation of network and security foundations for patterns found in the TIC 3.0 use cases.
The Traditional TIC Use Case is intended to provide guidance for how existing TIC 2.2 security capabilities can be used to implement TIC 3.0 capabilities. In our provided designs, we showed a deployment that follows CISA’s use case assumptions in which agency network traffic traverses a TIC access point when moving to and from external zones. In addition, we provided a revised design for when the TIC access point traverses connections to low trust zones only, like the Internet.
The TIC 3.0 Branch Office Use Case defines how network and multi-boundary security should be applied when agencies conduct work in more than one physical location, in which most of the information technology services, including generic web traffic, are traditionally provided by the agency campus.
The TIC 3.0 Remote User Use Case defines how network and multi-boundary security should be applied when an agency permits remote users on their network. A remote user is an agency user that performs sanctioned business functions outside of a physical agency premises.
Our commitment to the federal government
Google is committed to supporting federal government requirements and guidance to help them support their mission. We collaborated with several existing federal government customers on these supporting documents. We commit to regular updates to ensure our supporting documentation maintains consistency with the TIC program guidelines. For more information about our services and offerings specifically for the U.S. federal government, visit our website.
Google’s professional services team is ready to provide customized support to customers seeking to implement TIC 3.0 solutions on Google Cloud. For questions, reach out to your Google representative, or to https://cloud.google.com/contact.
If you have questions or need additional guidance please contact tic-initiative@google.com
