Preventing data breaches is an important priority when creating and managing database environments. Ensuring user and application passwords meet high security standards is crucial for reducing risk and helping to achieve compliance with best practices and regulatory standards.
To address these concerns, we are thrilled to announce the general availability of Local Users Password Validation feature for Cloud SQL for PostgreSQL and MySQL. It allows you to set up password rules for your local database users and can help better secure your databases. This feature is complementary to the existing Identity and Access Management (IAM) integration.
Password validation for PostgreSQL
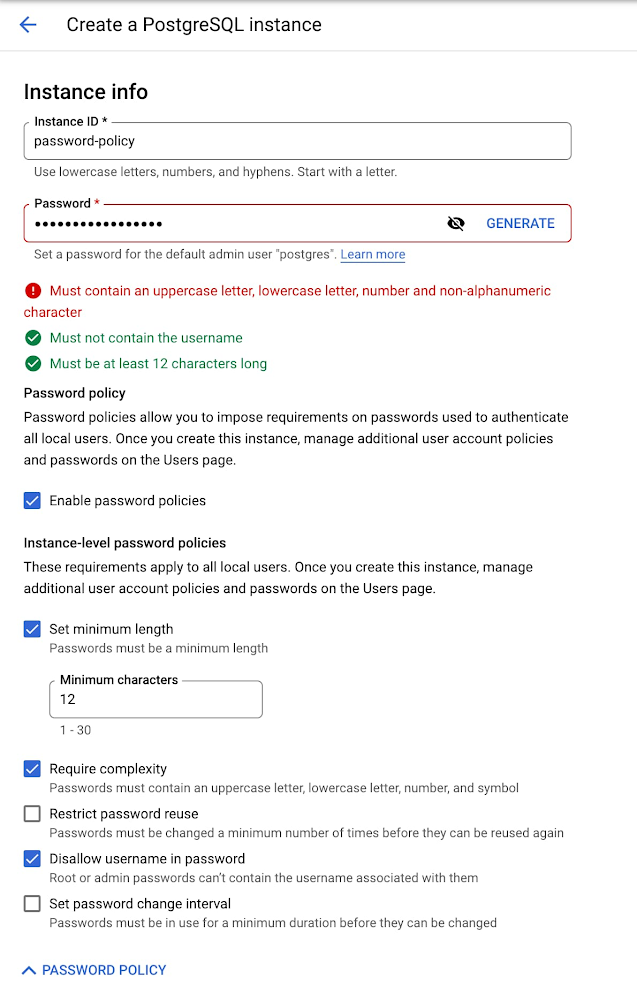
Password Validation settings on Instance level are now available for Cloud SQL for PostgreSQL. At the instance level, you can set rules to be applied to all local users (including the default postgres admin.) These configurations include:
-
Password complexity
-
Minimum number of characters required in a password
-
Number of times before a password can be reused
-
Prohibiting the use of a username in the password
-
Setting a minimum number of days after which the password can be changed
Here’s the new console user interface for the Instance Level Policy for PostgreSQL:
Password validation for MySQL
Password Validation for MySQL supports the existing password validation plugins capabilities and includes improvements to simplify your experience. We are introducing two levels of password settings in Cloud SQL for MySQL: Instance level password policy and User level password policy.
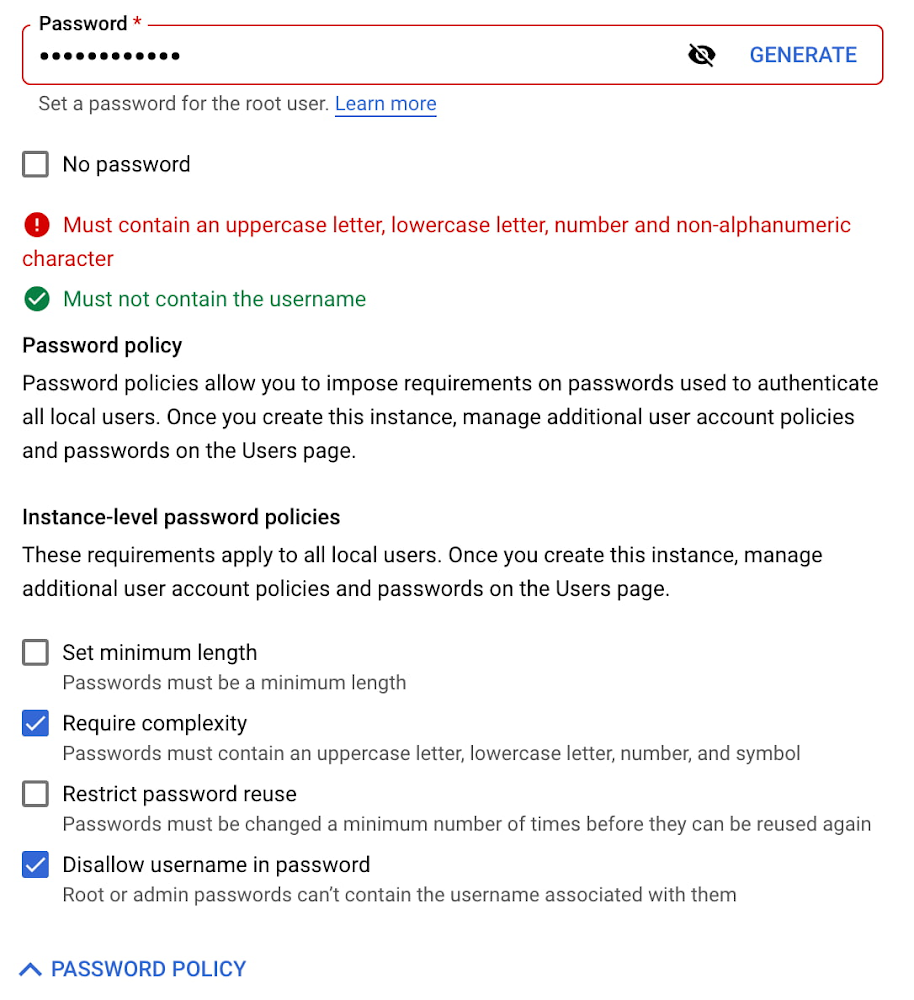
At the instance level, you can set rules to be applied to all local users (including the default root user.) These include:
-
Password complexity
-
Minimum number of characters required in a password
-
Number of times before a password can be reused
-
Prohibiting the use of a username in the password
Here’s the new console user interface for the Instance Level Policy for MySQL:
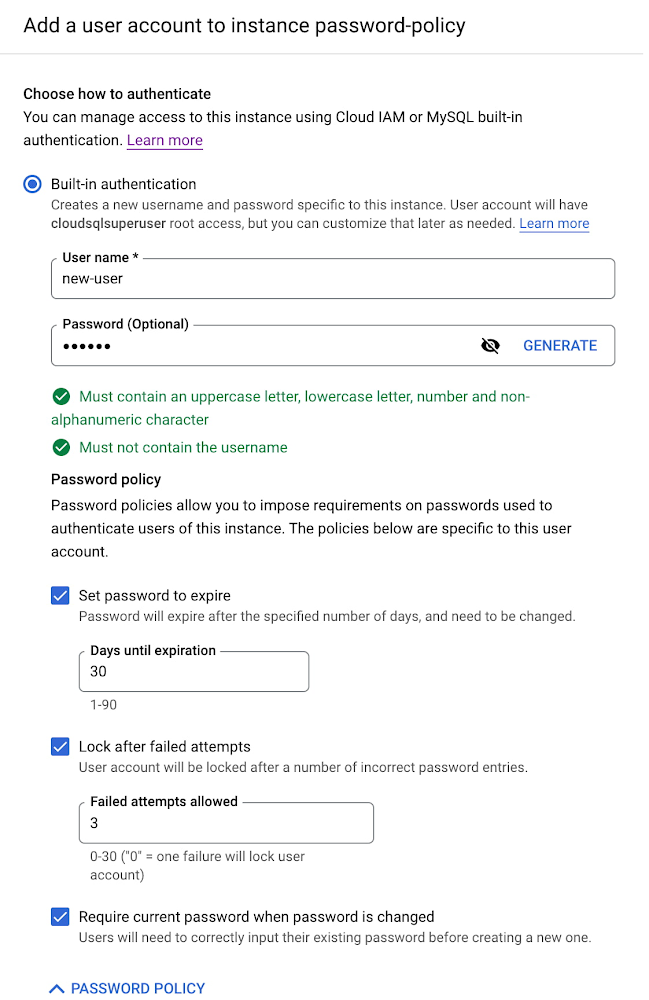
At the user level, you can set rules for a specific user. These rules include:
-
Password expiration
-
Maximum number of allowed failed login attempts
-
Password verification to require any password change to specify the current password
-
Dual password use
-
Generation of a random password
Here’s the new user interface for the User Level Policy for MySQL:
Using local user password validation with IAM
To understand how local user password validation works together with Cloud Identity and Access Management (IAM), let’s start by defining each of these authentication methods:
Cloud SQL integration with IAM enables Cloud SQL for PostgreSQL and MySQL end users and service accounts to connect to Cloud SQL instances using their IAM credentials. Once set up, users authenticate to the database by logging in to IAM. Behind the scenes, the service requests an authentication token from the IAM service and presents the token to the instance.
Local database users are created and managed locally within the database, enabling any person or application to access a database for data read, write, or update purposes. Database users own the objects they create in a database, such as tables, procedures, and storage locations. There are different types of users and levels of privileges that can be granted to each user.
Local database users and IAM users are complementary, and you can choose to use these authentication methods together or separately, depending on your authentication strategy.
We recommend using the centralized approach with IAM for Cloud SQL to help you better manage login access for users and service accounts to your databases. That said, there are use cases where managing local database users is still required, such as supporting legacy systems. It is important to mention that the password validation rules we are introducing today for local database users don’t apply to IAM users. The IAM service has its own password policy settings.
Local User Password Validation is now available to keep your Cloud SQL for PostgreSQL and MySQL instances even more secure and meet your compliance requirements. Learn more by reading Cloud SQL built-in database authentication and get started by creating a new instance with a password policy.